Security & Authentication
KAPPA-Automate uses OpenID to manage user authentication. Authentication can be done with built-in accounts created by an administrator or thanks to an existing authority (Azure AD for instance). User privileges are assigned at field level by an administrator.
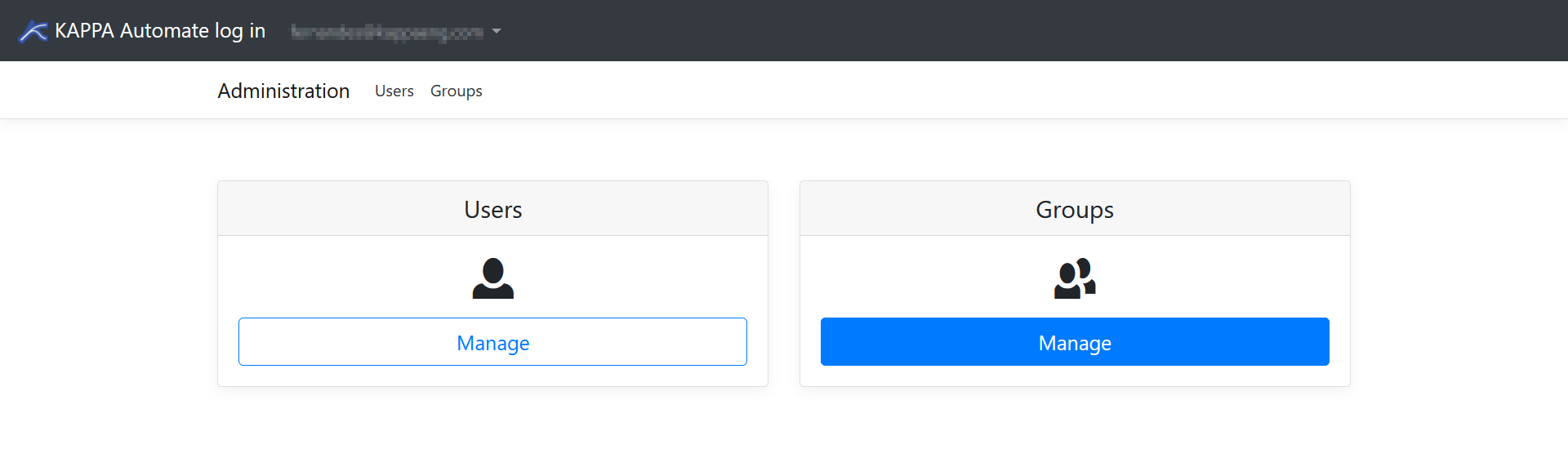
This can be done via two methods:
Users — Set permissions for each user individually.
Groups — Set permissions on a group that will be applied to all users who are added to it.
 |
In the Users window, you have several options available:
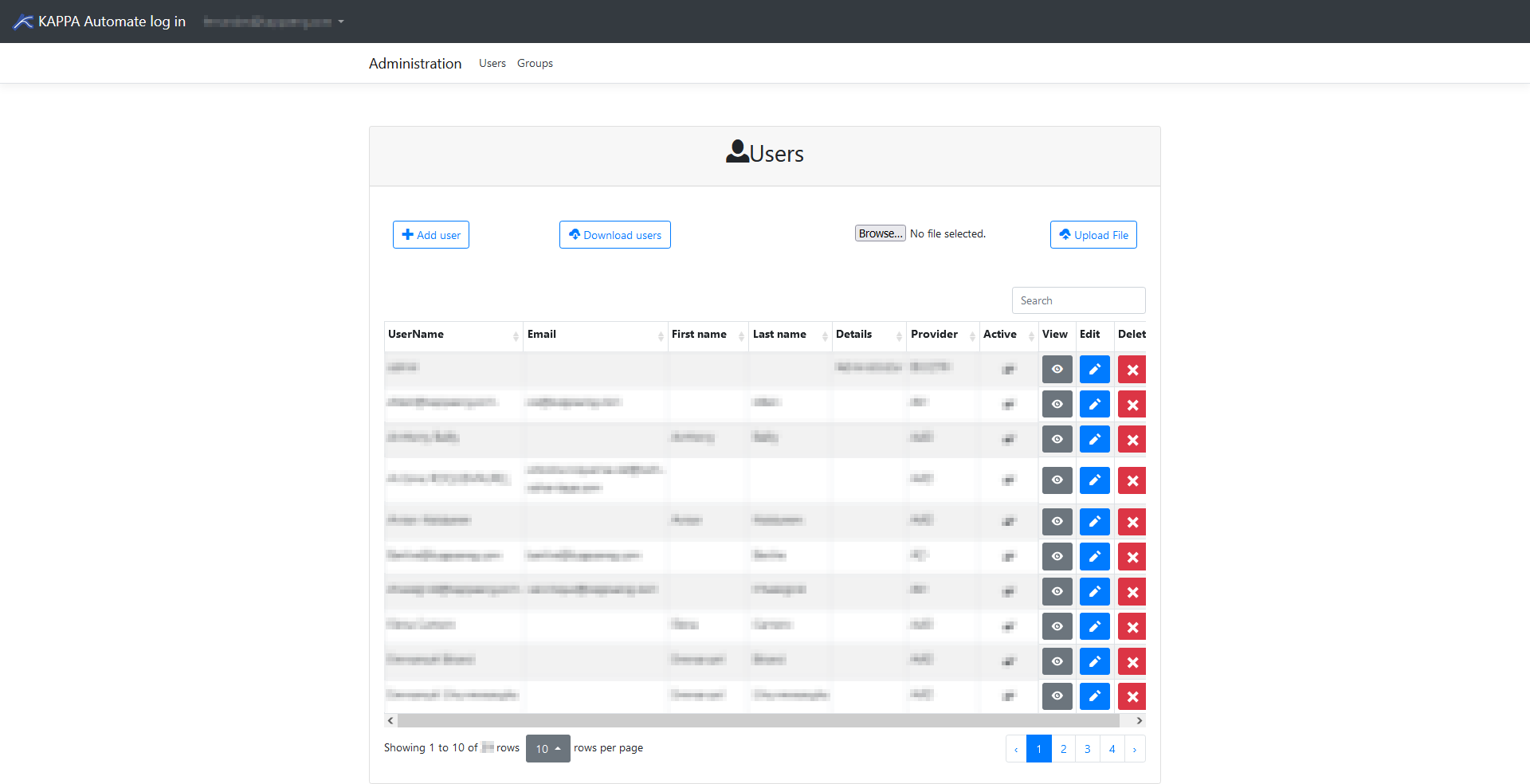 |
Add User
To add a user to KAPPA-Automate, fill out all the required fields for their profile and grant them relevant permissions. Once this has been done, click Save to confirm the action.
Download Users
Downloads a .json file with a list of all the users.
Browse and Upload File
You can import privileges from a .json file using the Browse and Upload File buttons.
View
Views the selected User's profile without the ability to edit.
Edit
Edits the selected User's profile and permissions.
Once changes have been made, click Save to implement and confirm. You can still cancel your changes if you have not yet clicked Save.
Delete
Delete the selected user profile.
In the Groups window, you have several options available:
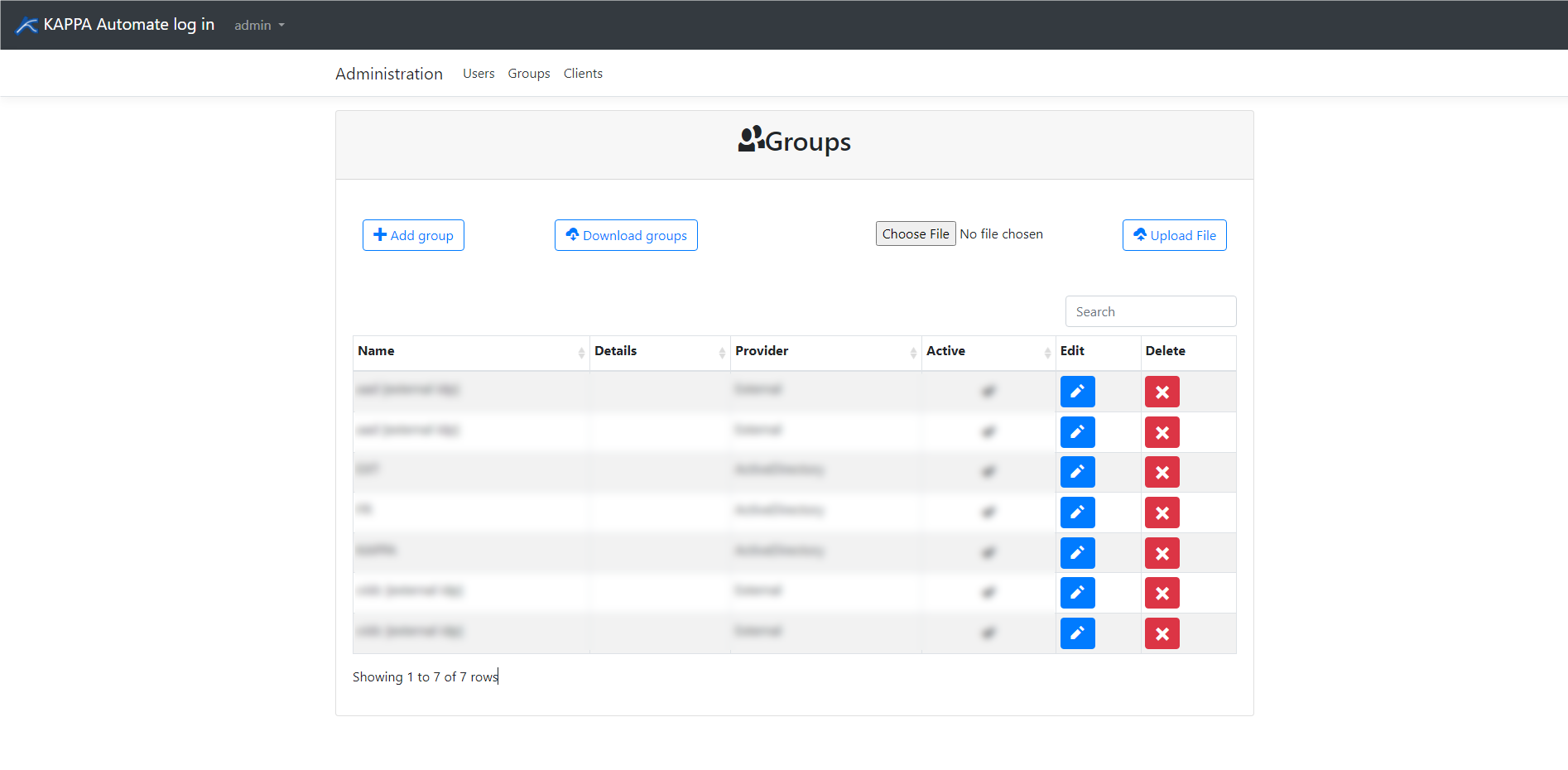 |
Add group
To add a user group to KAPPA-Automate, fill out all the required fields for their profile and grant them relevant permissions. Once this has been done, click Save to confirm the action.
Download groups
Downloads a .json file with a list of all the user groups.
Browse and Upload File
You can import privileges from a .json file using the Browse and Upload File buttons.
Edit
Edits the selected User group's profile and permissions.
Once changes have been made, click Save to implement and confirm. You can still cancel your changes if you have not yet clicked Save.
Delete
Delete the selected user group profile.
Different user rights can be defined in KAPPA-Automate:
General permissions
Field access
Data source access
Groups
General permissions are applicable to a specific user or group.
There are four general permissions, described in the following table:
Permission | Description | K-A access |
|---|---|---|
K-A read & connect | Allows the user to connect to K-A. | Connect allowed & list of fields |
K-A full control | Allows the user to administrate processes and security on K-A. | |
Fields delete & create | Allows the user to create and delete fields on K-A. | Delete/create new field¹ |
Data sources delete & create | Allows the user to create and delete data sources on K-A. | Delete/edit/create new data source |
¹ When a field is created, the owner will have a new specific field access for this field (level delete).
It is possible to either allow or deny access to one or several general permissions. The Deny setting will ensure that the user does not have access to a specific general permission, even if he/she belongs to a group that has this access. You can specify general permissions at the group or user level.
There are four different accesses that can be given to a field:
Denied
Read
Create
Delete
If no specific access privilege has been set on a particular field, the default field access will be applied on that field.
The Denied privilege will override any other permission previously granted.
You can specify field accesses at the group or user level.
There are two different accesses that can be given to a data source:
Denied
Allowed
If no specific access privilege has been set on a particular data source, the default data source access will be applied on that data source.
The Denied privilege will override any other permission previously granted. You can specify data source accesses at the group or user level.
It is possible to create as many groups as possible. This way it is not necessary to manually create all the corresponding users. A single user can belong to one or several groups.
There are four built-in groups:
Admins
Power users
Users
Denied
K-A full control | K-A read & connect | Fields delete & create | Data sources delete & create | |
|---|---|---|---|---|
Admins | Allow | Allow | Allow | Allow |
Power users | Allow | Allow | ||
Users | Allow | |||
Denied | Deny | Deny | Deny | Deny |